Pierre Lescure, former CEO of French broadcaster Canal +, has delivered to the French minister of culture and communication his report “Contribution aux politiques culturelles à l’ère numérique” (i.e. contribution to cultural policies in the digital area). Obviously, among the 88 recommendations, numerous proposals tackle copyright issues. These recommendations got the headlines of French press.
Pierre Lescure and his team have deeply analyzed the current French graduated response, its organization HADOPI, and its efficiency. Let’s navigate among the 700 page document and highlights some interesting points.
In section A-5: The release window
The report highlights that the audience wants the pieces of content as early as possible. furthermore, VOD is drastically increasing. Thus, they propose to reduce the current release window of VOD by one month. Interestingly, they would offer this earlier release only to “good citizen” operators.
Plus précisément, il est proposé d’avancer la fenêtre de la vidéo à la demande, éventuellement en réservant cette mesure aux services les plus vertueux, c’est-à-dire à ceux qui acceptent de prendre des engagements volontaristes en termes de financement de la création et d’exposition de la diversité.
Furthermore, they propose the concept of premium week end when a piece of content would be available as VOD one or two weeks after theatrical release for 30€ (40$).
Section A-14 tackles the issue of DRM. They propose to extend the scope of the DAVDSI law to games and public domain content. They recommend also to create an open standard for DRM.
Personal note: the problem with open standard is that it cannot enforce a compliance and robustness regime that is mandatory for any DRM to be efficient  .
.
They highlight that DRM and French right to private copy are not well co-existing.
Section B-7 tackles the issue of the private copy levy.
As cloud computing is becoming more and more present, storage in the cloud will become prevalent. Therefore, the current private copy levy will become useless. Thus, the report suggests to create a levy for every connected device regardless of its internal storage capabilities.
In section C2: “Appraisal of the graduated response”.
La réponse graduée (articles L.331-24 et suivants du CPI) a pour fondement non pas l’acte de contrefaçon en lui-même, mais le manquement à l’obligation de surveillance du titulaire de l’abonnement Internet de son poste d’accès …
La notion de négligence caractérisée permet ainsi, au terme de la procédure de réponse graduée, de sanctionner le titulaire de l’abonnement sans avoir la preuve qu’il est bien l’auteur du délit de contrefaçon, dès lors qu’il n’a pas pris les dispositions pour sécuriser sa ligne.
They highlight that the cornerstone of the French graduated response is not the counterfeiting act but the fact of characterized negligence to secure his/her Internet access. Being negligent to secure the network does not mean the owner of the network was the infringer.
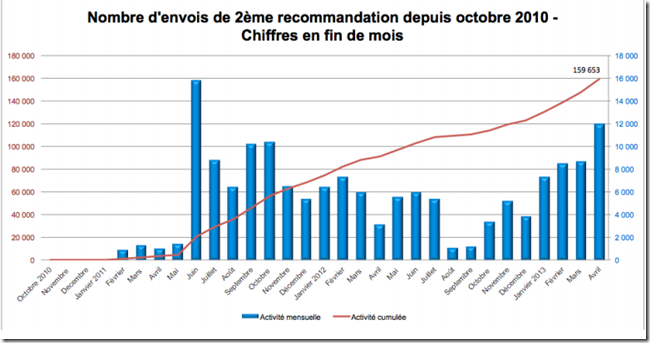
At February 2013, content owners detected 35 millions for 4.7 millions IP addresses. 1.6 millions first warning and 139,000 second warnings were issued with 29 cases passed to the Court. Only two cases were sentenced with a 150€ fine. In 2012, the direct cost of the graduated cost was 6M$, with an additional bill of 2.5Me from the three main ISPs. This evaluation does not include the cost of TMG detecting the supposed infringing IP addresses that is bared by the content owners.
They must conclude that the efficiency is mixed. The use of P2P has visibly declined by 40% in three years. Nevertheless, this may just mean that the traffic moved to direct download/streaming sites that HADOPI does not monitor.
In section C-3: “Lightening the graduated response”
The report acknowledges that suppressing the graduated answer would have many advantages. nevertheless, the disadvantages are more important. The report proposes to clarify the concept of “characterized negligence”. You would have to put something in place, you not to be successful. They propose also to rather focus on the counterfeiting rather than on the negligence. The counterfeiting act should be proven and for monetary gain.
Dans l’immédiat, il pourrait être demandé aux Parquets de n’engager des poursuites pour contrefaçon que lorsqu’ilexiste des indices sérieux et concordants tendant à prouver l’existence d’un enrichissementpersonnel ou collectif, dans le cadre d’un réseau contrefaisant.
The educational element of the graduated response should be enhanced. Thus, the ultimate punishment, i.e. suppression of Internet access, should be replaced by throttling. Furthermore, the fine should be reduced from 1,500€ to 60€.
The report proposes to close the HADOPI organization and forward its mission to the Conseil Supérieur de l’Audiovisuel (High Council of Audiovisual). We anticipated that in August 2012.
Section C-4: “the fight against online commercial piracy” is going in the right direction. It clearly highlights that direct download, streaming and referee sites are making money through piracy, estimated between 52 to 71M€ each year in France. According to the report, these sites are the real money makers of digital piracy. Despite the laws exist, suing these site owners is difficult. The State should be proactive in this fight.
Section C-5: “The responsibility of hosting sites”. Currently, European and French laws imply that the hosting site cannot be responsible:
- if it was not aware that content was infringing
- if it did not take down infringing content once notified.
La responsabilitécivile ou pénale des hébergeurs ne peut être engagée « s’ils n’avaient pas effectivement connaissance » du caractère illicite des contenus stockés ou « si, dès le moment où elles en ont eu cette connaissance, elles ont agi promptement pour retirer ces données ou en rendre l’accès impossible ».
The report does not recommend to modify this status. Nevertheless, it recommends to facilitate good practices such as using fingerprint to detect illegal content (The French INA signature is highlighted). The report recommends that the French State support a common initiative to set up an organization that would create a database of reference fingerprints and send take down notifications to sites.
In Section C-6, the report recommends that search engines should present the legal offers in a predominant position compared to counterfeiting offers. Currently, search engines have in Europe light responsibilities in this field.
Section C-7 highlights the role of payment organizations and advertisement agencies. they indirectly facilitate and benefit from digital piracy. The report calls these intermediaries to be good citizens. Google has already proven that it may accept to play this game.
Section C-8 tackles the issue of blocking a site and domain names. Although possible with French regulation, the report does recommend to use them only as ultimate solution.
Conclusion:
- Is HADOPI dead? It seems that this time, it is a serious blow against it. It is only a report, not a set of decisions. We know the French minister of culture is not HADOPI-friendly. Thus the likelihood of its near death is high.
- Is the French graduated response dead? It will continue, in its current form or in a new way, regardless of its future hosting organization.